需求:直接替换阿里云购买的 SSL VPN,硬刚……


openvpn 版本:2.4.9-1.el7
ease-rsa 版本:3.0.7-1.el7
openvpn-auth-ldap 版本:2.0.3-17.el7
yum install -y openvpn easy-rsamkdir -p /etc/openvpn/easy-rsa/keyscp /usr/share/doc/openvpn-2.4.9/sample/sample-config-files/server.conf /etc/openvpn
cp -rf /usr/share/easy-rsa/3.0/* /etc/openvpn/easy-rsa/
cp /etc/openvpn/easy-rsa/openssl-easyrsa.cnf /etc/openvpn/easy-rsa/openssl.cnf
openvpn --genkey --secret /etc/openvpn/ta.key[root@cjz openvpn]# cd /etc/openvpn/easy-rsa/
[root@cjz easy-rsa]# ./easyrsa init-pki
init-pki complete; you may now create a CA or requests.
Your newly created PKI dir is: /etc/openvpn/easy-rsa/pki
[root@cjz easy-rsa]# ./easyrsa build-ca
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Enter New CA Key Passphrase: #在此要输入ca的密码:(ca.com),需要输入两次。
Re-Enter New CA Key Passphrase:
Generating RSA private key, 2048 bit long modulus
........+++
..+++
e is 65537 (0x10001)
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [Easy-RSA CA]:limikeji #此处要输入组织:(Open××× CERTIFICATE AUTHORITY)
CA creation complete and you may now import and sign cert requests.
Your new CA certificate file for publishing is at:
/etc/openvpn/easy-rsa/pki/ca.crt
[root@cjz easy-rsa]# ./easyrsa gen-req cjzshilong
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
............+++
..........................................................+++
writing new private key to '/etc/openvpn/easy-rsa/pki/easy-rsa-1945.QkcdZs/tmp.plZnLa'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [cjzshilong]:
Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa/pki/reqs/cjzshilong.req
key: /etc/openvpn/easy-rsa/pki/private/cjzshilong.key
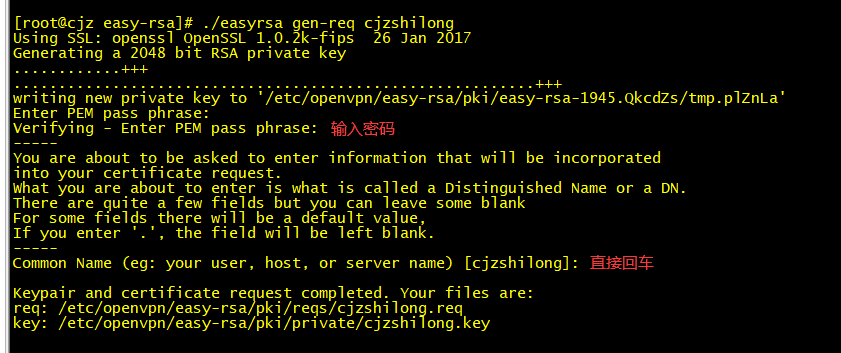
[root@cjz easy-rsa]# ./easyrsa sign-req server cjzshilong
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.
Request subject, to be signed as a server certificate for 825 days:
subject=
commonName = cjzshilong
Type the word 'yes' to continue, or any other input to abort.
Confirm request details: yes
Using configuration from /etc/openvpn/easy-rsa/pki/easy-rsa-1972.yu5li8/tmp.z0dO8n
Enter pass phrase for /etc/openvpn/easy-rsa/pki/private/ca.key:
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'cjzshilong'
Certificate is to be certified until Aug 23 02:29:57 2022 GMT (825 days)
Write out database with 1 new entries
Data Base Updated
Certificate created at: /etc/openvpn/easy-rsa/pki/issued/cjzshilong.crt
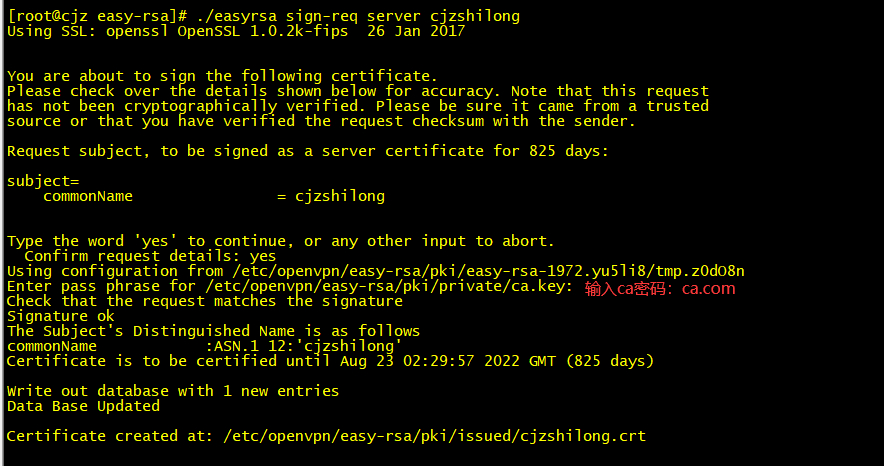
[root@cjz easy-rsa]# ./easyrsa build-client-full test
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
................................................................+++
.........+++
writing new private key to '/etc/openvpn/easy-rsa/pki/easy-rsa-2119.2QIQRw/tmp.k6ehaI'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
Using configuration from /etc/openvpn/easy-rsa/pki/easy-rsa-2119.2QIQRw/tmp.nFtxKF
Enter pass phrase for /etc/openvpn/easy-rsa/pki/private/ca.key:
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'test'
Certificate is to be certified until Aug 23 02:33:16 2022 GMT (825 days)
Write out database with 1 new entries
Data Base Updated
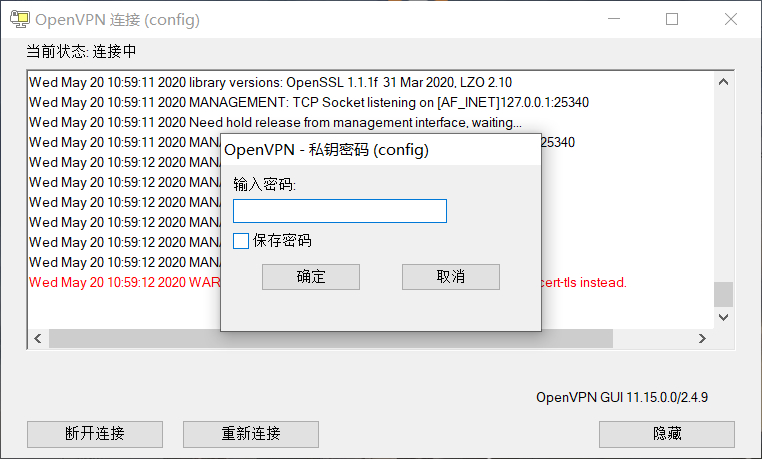
注:生成客户端用户的时候会提示设置密码,可以直接回车密码为空,也可以输入密码,待客户端连接时需要输入密码。
ls -l /etc/openvpn/easy-rsa/pki/issued/test.crt
ls -l /etc/openvpn/easy-rsa/pki/private/test.key
vim /etc/sysctl.conf[root@cjz easy-rsa]# sysctl -pport 1194 #端口:1194
proto udp #协议使用:UDP
dev tun
ca /etc/openvpn/easy-rsa/pki/ca.crt #此处配置的是绝对路径
cert /etc/openvpn/easy-rsa/pki/issued/cjzshilong.crt
key /etc/openvpn/easy-rsa/pki/private/cjzshilong.key # This file should be kept secret
dh /etc/openvpn/easy-rsa/pki/dh.pem
server 10.8.0.0 255.255.255.0 #内网服务器虚拟地址
ifconfig-pool-persist ipp.txt
push "route 172.16.0.0 255.255.0.0"
push "redirect-gateway def1 bypass-dhcp" #使客户端所有网络通信通过vpn
push "dhcp-option DNS 223.5.5.5" #配置DNS
push "dhcp-option DNS 114.114.114.114"
keepalive 10 120
tls-auth /etc/openvpn/ta.key 0 # This file is secret
cipher AES-256-CBC
comp-lzo
max-clients 100 # 最大客户端连接数量
user openvpn
group openvpn
persist-key
persist-tun
status openvpn-status.log # 状态日志
log-append /var/log/openvpn/openvpn.log # 开启OpenVpn日志
verb 3
mute 20
explicit-exit-notify 1
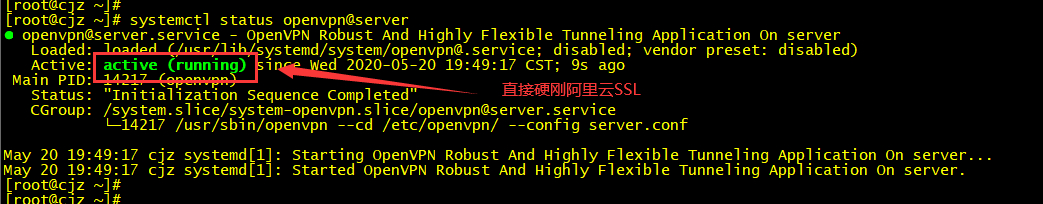
systemctl start openvpn@server[root@cjz ~]# ps -aux | grep openvpn
openvpn 11941 0.0 0.1 77636 4940 ? Ss May19 0:01 /usr/sbin/openvpn --cd /etc/openvpn/ --config server.conf
root 12992 0.0 0.0 112708 988 pts/2 S+ 10:44 0:00 grep --color=auto openvpn
查看安装 openvpn 后的网卡状态:
[root@cjz ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:16:3e:10:39:70 brd ff:ff:ff:ff:ff:ff
inet 172.16.16.55/24 brd 172.16.16.255 scope global dynamic eth0
valid_lft 315295137sec preferred_lft 315295137sec
8: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 100
link/none
inet 10.8.0.1 peer 10.8.0.2/32 scope global tun0
valid_lft forever preferred_lft forever
windows 64 位的 openvpn 版本为:2.4.9 可以从官网上下载
下载链接:https://openvpn.net/community-downloads/
tese.crt test.key ca.crt ta.key[root@cjz ~]# cd /etc/openvpn/client/
[root@cjz client]# ll
total 20
-rw------- 1 root root 1159 May 19 18:22 ca.crt
-rw------- 1 root root 636 May 19 18:22 ta.key
-rw------- 1 root root 4418 May 19 18:22 test.crt
-rw------- 1 root root 1834 May 19 18:22 test.key
client
dev tun
proto udp
resolv-retry infinite
nobind
remote 182.x.x.141 1194 #此处要更换成出口的公网IP地址
ns-cert-type server
comp-lzo
ca ca.crt
cert test01.crt
key test01.key
tls-auth ta.key 1
keepalive 10 120
persist-key
persist-tun
verb 5
redirect-gateway
route-method exe
route-delay 2
status test01-status.log
log-append test01.log
安装 Openvpn 2.4.9 x86_64 后,需要找到客户端安装目录下的 config 文件夹,清空 config 文件夹,然后将客户端证书和客户端配置文件复制到 config 文件夹下
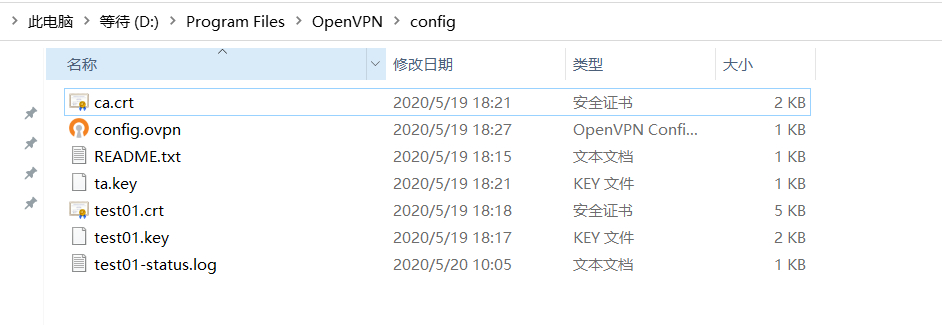
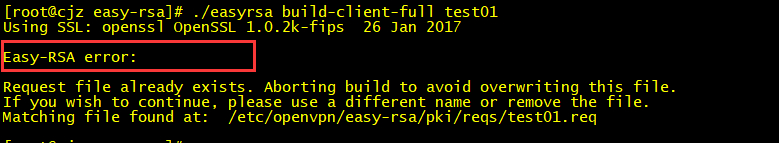
[root@cjz easy-rsa]# rm -f /etc/openvpn/easy-rsa/pki/reqs/test01.req
[root@cjz easy-rsa]# rm -f /etc/openvpn/easy-rsa/pki/private/test01.key
./easyrsa revoke test./easyrsa gen-crlsystemctl stop openvpn@server
systemctl start openvpn@server
#开启NAT转发
iptables -I FORWARD -j ACCEPT ###开启所有转发
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
OpenVPN 服务端集成的 OpenLDAP 认证,这样能够使客户端用户在连接 VPN 时直接使用统一的 OpenLDAP 账号
yum install openvpn-auth-ldap -y
主要会安装 /usr/lib64/openvpn/plugin/lib/openvpn-auth-ldap.so 文件,和生成 /etc/openvpn/auth/ldap.conf 文件。
配置 vim /etc/openvpn/auth/ldap.conf
<LDAP>
URL ldap://172.16.16.4:389
BindDN cn=manager,dc=limikeji,dc=com
Password limikeji.com
Timeout 15
TLSEnable no
FollowReferrals no
</LDAP>
<Authorization>
BaseDN "dc=limikeji,dc=com"
SearchFilter "uid=%u"
RequireGroup false
<Group>
BaseDN "ou=group,dc=limikeji,dc=com"
SearchFilter "cn=chanpinyanfabu"
MemberAttribute uniqueMember
</Group>
</Authorization>
注意上面的 ldap.conf 中如果设置
RequireGroup true以及 Group 的配置实际我们期望是必须是 LDAP 中的名称为 VPN 的组下的用户才可以登录 VPN。但根据这个 ISSUE,当前 2.0.3 的 openvpn-auth-ldap 不支持。因此如果只想限制 LDAP 中某些用户可以使用 VPN 的话,只能设置RequireGroup fals,然后可以在 SearchFilter 中做一些文章,比如(&(uid=%u)(ou=vpn))即只有用户的 ou 字段为(vpn)的才可以。
配置 /etc/openvpn/server.conf,添加如下:
...
plugin /usr/lib64/openvpn/plugin/lib/openvpn-auth-ldap.so "/etc/openvpn/auth/ldap.conf"
client-cert-not-required
...
client-cert-not-requir 不再需要客户端证书,将改为使用 OpenLDAP 中的用户认证client
dev tun
proto udp
resolv-retry infinite
nobind
remote 182.x.x.141 1194 #此处要更换成出口的公网IP地址
ns-cert-type server
comp-lzo
ca ca.crt
;cert test01.crt
;key test01.key
tls-auth ta.key 1
keepalive 10 120
persist-key
persist-tun
verb 5
auth-user-pass
redirect-gateway
route-method exe
route-delay 2
status OpenVpnClient-status.log
log-append test01.log
cert client.crt 和 ;key client.key 不再需要客户端证书 client.crt 和秘钥 client.keyns-cert-type server 和 auth-user-pass 是新加入的配置开启了用户名密码认证此时集成 LDAP 的 OpenVPN 客户端认证文件目录如下:
配置参考 :
[3] https://open.weave.pub/install_openvpn
[4] https://blog.frognew.com/2017/09/openvpn-integration-ldap.html
LDAP 配置参考:?
[5] https://github.com/threerings/openvpn-auth-ldap/wiki/Configuration
FQA:?
[6] https://forums.openvpn.net/viewtopic.php?t=2156